BianLian: The face-changing ransomware menace
There’s no shortage of weird brand names in the world of cybercrime. Threat actors like to intimidate people and project the image of a strong and stealthy threat. Something called "Bob's ransomware" just isn't as disturbing as REvil or Hive, which both have a disturbing 'Resident Evil' feel to them. And then there's Rhysida, which is an appropriate name for ransomware, but only to those who know what a Rhysida is. I had to look it up. And RansomHub just sounds like a creepy dating app.
Today we're looking at a ransomware threat called BianLian, and this group has made a naming decision that I can respect. The original Bian Lian, pronounced “bee-yen lee-yen,” is a traditional Chinese art form embedded in Sichuan opera. The name translates to “face changing,” referring to the performers’ rapid transitions between theatrical masks that depict different characters and emotional states. Sleight of hand and other techniques are used to change masks almost instantaneously. You can see an example in the video below.
It's like magic.
The threat actor BianLian is nothing like the beautiful art of Bian Lian, but the 'face changing' name is on point.
BianLian origin story
BianLian-associated infrastructure was detected as early as December 2021, and experts believe the group was actively developing its toolset at that time. The ransomware emerged in July 2022, and by the end of August, the group had tripled its command and control (C2) infrastructure and had listed victims in several industries.
Some experts speculated that BianLian was a rebrand or offshoot of the Pysa group due to similar tactics, techniques, and procedures (TTPs) and an observable timeline of activity. No official advisories or detailed analyses have published evidence to support this theory. On the contrary, the researchers at Recorded Future theorized that BianLian was a true newcomer to the ransomware scene in 2022. They published these observations at the time:
…For all intents and purposes, the BianLian group appears to represent a new entity in the ransomware ecosystem. Furthermore, we assess that the BianLian actors represent a group of individuals who are very skilled in network penetration but are relatively new to the extortion/ransomware business.
…
While the actor has proven themselves proficient at compromising a victim network, we have seen the actor:
- Mistakenly sending data from one victim to another.
- Possessing a relatively stable backdoor toolkit, but have an actively developing encryption tool with an evolving ransom note.
- Long delays in communications with victims.
- Through the groups own admission on their onion site, the business side of their infrastructure is unreliable.
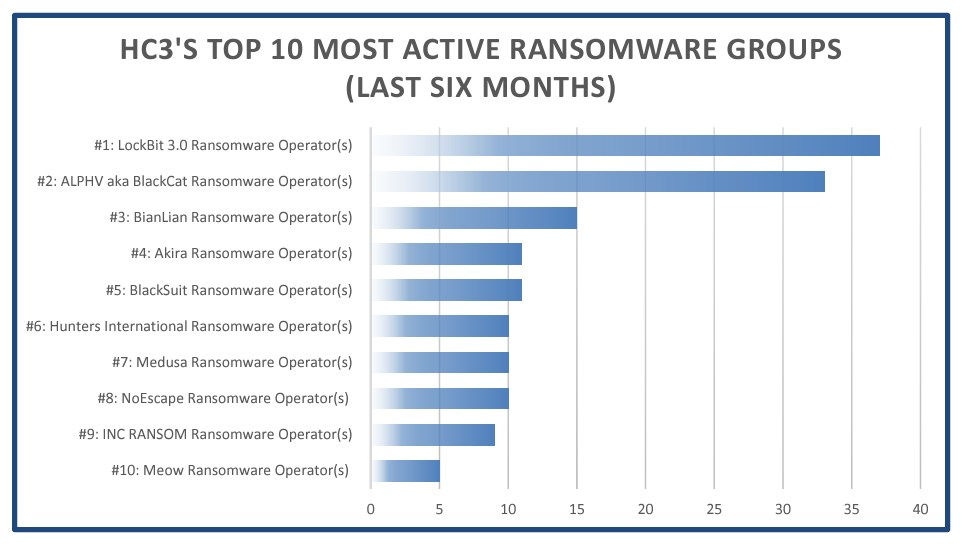
BianLian has matured since then, and the group may have picked up new members who are more experienced in ransomware operations. What we know for sure is that in roughly two years of operations, BianLian has victimized companies of all sizes in all parts of the world.
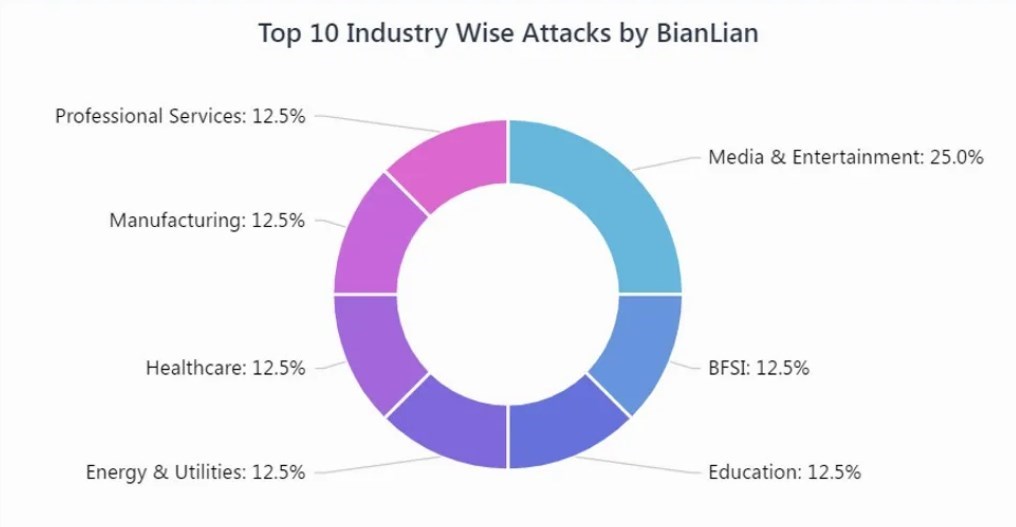
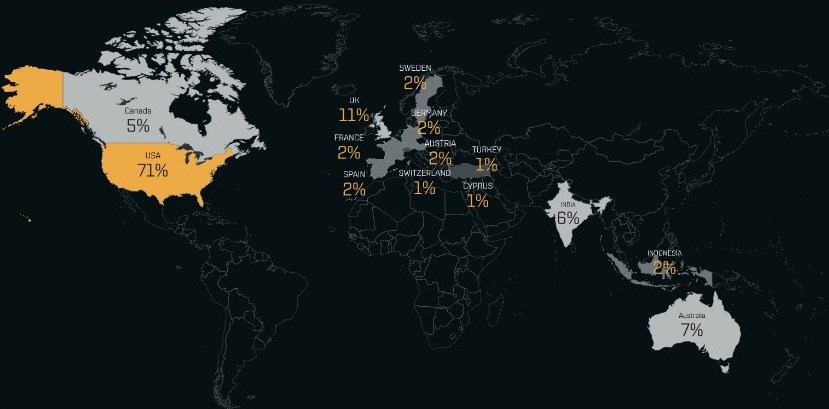
The exact location of the BianLian threat actors appears to be unknown, but the group uses the Russian language in their communications, and they do not target Russian-speaking countries. Their threat activity has focused heavily on victims in the United States (U.S.), Australia, and Europe. The bulk of these attacks are against manufacturers and healthcare organizations in the U.S. The group doesn't seem to be affiliated with an ideology or a nation-state. BianLian is just out to make money, and their profile here is typical for financially motivated ransomware groups. Politics and socio-economic issues aside, the group wants to operate from a location that doesn't cooperate with law enforcement in the countries they target.
BianLian and encryption
BianLian proved worthy of its name over the last few years. The ransomware is written in Go (or GoLang), which has simplified the process of updating the code to improve functionality, stealth, and persistence. This ongoing development led to several versions of BianLian ransomware, almost always in response to new security measures. The group has also finessed the code to improve the speed and performance of its toolset. The most noticeable change, however, was the group's operational shift to data exfiltration over encryption in 2023.
BianLian ransomware had a few vulnerabilities when it was launched in 2022. The early versions used flawed encryption algorithms or broken implementation, which made it possible to decrypt files without paying the ransom to get a decryption key. In January 2023, researchers from Avast released a free BianLian decryptor to the public, resulting in massive losses for the threat actor. BianLian ransomware also relied on communication with command and control (C2) servers for encryption keys, and blocking access to those servers would block the encryption process. A network monitoring tool could perform that task with simple automation.
BianLian responded to these flaws and the publicly available decryptor by improving the stealth and backdoor persistence capabilities of its toolset, including the C2 communication, and leaning in on the data exfiltration side of the threat. The use of 'extortion-less ransomware' is growing, as many threat actors have realized that companies are less willing to pay for decryption than they are to maintain the privacy of their data. Most ransomware groups still use encryption as an additional layer of extortion, but the stolen data is the real money these days.
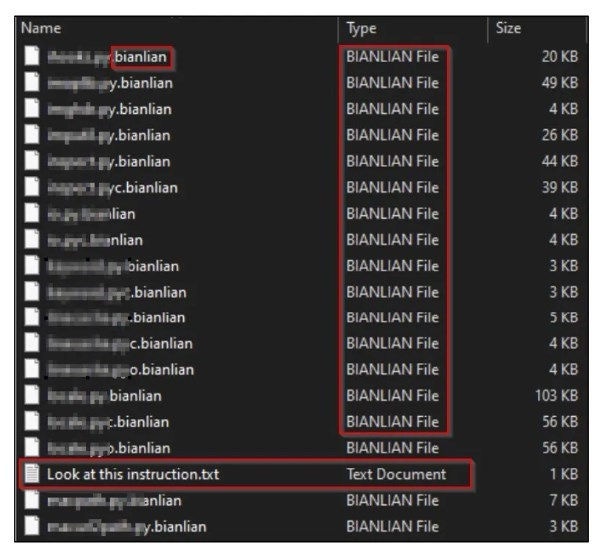
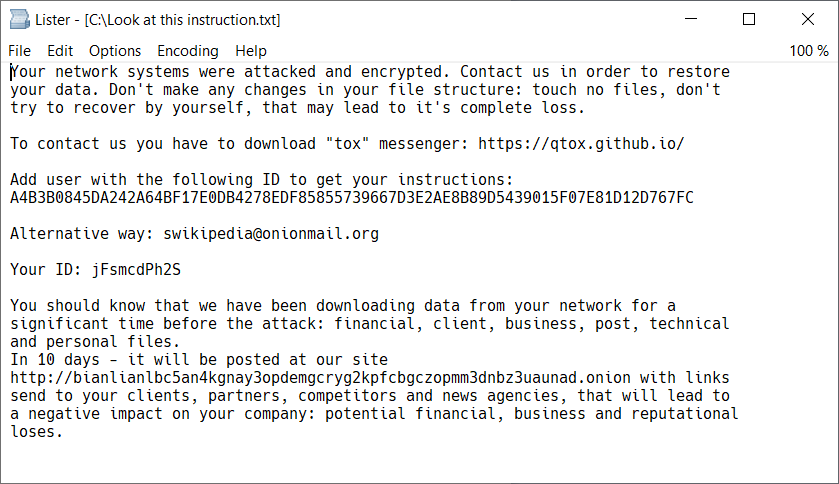
When BianLian does execute a ransomware binary, the files are renamed and a ransom note is generated.
There's no way to know how much BianLian has cost the U.S. or global economy, but we can round it up to "a lot." In the U.S., the average cost of a healthcare breach reached nearly $11 million last year. The per-incident cost for manufacturers is lower, but continues to rise. These sectors are the preferred targets for BianLian and many other threat actors.
How the BianLian attack works
BianLian ransomware infections often start with a phishing email, compromised credentials, or a vulnerability exploit. These tactics are common for threat actors, so there's nothing special about BianLian when it comes to this. But we should take this opportunity to remind ourselves (and everyone we know) that protecting our credentials is of massive importance. Lists like RockYou2024 and Collection #1 provide attackers with the potential to create new lists with billions of unique combinations of emails and passwords to be used in automated attacks. Credentials have always been valuable to threat actors, and stealing, guessing, or calculating their way to a working set of credentials is much easier with the help of AI. Many threat actors will simply purchase credential sets from others that specialize in selling access to compromised systems.
Once BianLian has infiltrated a system, it establishes persistence, control, and redundancy by deploying multiple backdoors that also act as loaders. The BianLian backdoor will download and run additional malware on the system, and it contains the information needed to communicate with the C2 servers. This backdoor allows attackers to run commands and exfiltrate data as desired, which makes it a significant component of the BianLian attack.
After the backdoors and other tools are established, BianLian attempts to escalate account privileges and disable security policies. The group uses legitimate system utilities to move laterally through the network to find and steal data using a custom data exfiltration tool they share with Makop ransomware. At this point, the attack may execute an encryption binary. If this is unsuccessful, they will just ransom the stolen data:
“Our business depends on the reputation even more than many others. If we will take money and spread your information- we will have issues with payments in future. So, we will stick to our promises and reputation. That works in both ways: if we said that we will email all your staff and publicly spread all your data- we will.” (Via Redacted)
The BianLian group customizes these messages, crafting them in a way that increases the pressure on the victim. These custom messages usually reference the legal ramifications and regulatory issues facing the company if the data breach became public. This information might be pulled from the data that has been exfiltrated, or the group may be researching the victims in some other way.
In April 2024, the U.S. Department of Health and Human Services reported BianLian as the third-most prolific threat actor against the public healthcare sector.
BianLian friends and family
There's no strong evidence that BianLian is a rebrand or an offshoot of another group. There is some overlap with other ransomware groups, but only in the most commonly used TTPs:
TTPs |
BianLian |
REvil |
Darkside |
Double Extortion |
Yes |
Yes |
Yes |
Data Exfiltration |
Yes |
Yes |
Yes |
Use of RDP |
Yes |
Yes |
Yes |
Use of PowerShell |
Yes |
Yes |
Yes |
That's not to say that BianLian operates alone. The group shares a data exfiltration tool with the Makop ransomware group, which may indicate a collaboration or a shared resource pool. BianLian also joined the White Rabbit and Mario Ransomware groups in a joint extortion campaign in December 2023. You can find the details of this campaign here.
TTPs |
BianLian |
White Rabbit |
Mario |
Makop |
Double Extortion |
Yes |
No |
No |
Yes |
Data Exfiltration |
Yes |
Yes |
Yes |
Yes |
Use of RDP |
Yes |
Yes |
Yes |
Yes |
Custom .NET Tools |
Yes |
No |
No |
Yes |
Collaboration with Other Groups |
Yes |
Yes |
Yes |
No |
Use of PowerShell |
Yes |
Yes |
Yes |
Yes |
Wrapping it up
BianLian just wants to sell your data, and more than anything else, they want to sell it back to you. They assume you will want the data more than anyone else, and you'll pay more than anyone else. If you won't pay them, they are happy to sell to someone else. It doesn't matter who pays them as long as they have enough money to buy more stolen credentials so they can steal more data. Maybe they'll steal yours again. Maybe they already have.
The beautiful art of Bian Lian is all about astonishing the audience with surprising twists and colorful masks. Don't let this ugly ransomware group surprise you with its next trick. Protect your credentials, keep your software updated, and make sure your company has solid ransomware protection in place.
Did you know ...
Barracuda research has found that most organizations have experienced a ransomware attack, and a third have been hit twice or more. Barracuda offers solutions that defend your data from ransomware and other attacks, including the most sophisticated AI-enhanced threats. Visit our ransomware solution page to download our free ransomware protection checklist and our latest research on ransomware in the age of AI.

The Ransomware Insights Report 2025
Risultati chiave sull'esperienza e l'impatto del ransomware sulle organizzazioni a livello mondiale
Iscriviti al blog di Barracuda.
Iscriviti per ricevere i Threat Spotlight, commenti del settore e altro ancora.

Sicurezza della vulnerabilità gestita: correzione più rapida, meno rischi, conformità più semplice
Scopri quanto può essere facile individuare le vulnerabilità che i criminali informatici vogliono sfruttare