
Lessons from Black Basta’s collapse
How leaked chats, law enforcement pressure and affiliate migration exposed the resilience of the ransomware ecosystem
Takeaways
- Black Basta’s collapse disrupted a name, not the underlying criminal capabilities, which quickly reappeared through affiliate migration and code reuse.
- Leaked operational data significantly strengthens investigations. Correlating chat logs with victim reports, blockchain data and intrusion timelines turned fragmented intelligence into actionable law‑enforcement evidence.
- Healthcare attacks accelerate scrutiny and consequences. Attacks on critical infrastructure change the risk calculus for both threat actors and defenders.
Black Basta (BlackBasta, Blackbasta, Basta, Vengeful Mantis) was a top-tier ransomware brand until its collapse in early 2025. The group collected at least $107 million in ransomware payments (based on blockchain tracing) from early operations in 2022 through late 2023. Black Basta was a global law enforcement priority for years prior to its disappearance, and investigators have continued to search for clues and evidence to bring group members to justice. Recent headlines reveal this work is getting results.
The group is widely regarded as a rebrand or offshoot of the Conti ransomware group that went dark in May 2022. Analysts saw strong overlaps in the tools and operations of the two groups, and blockchain tracing later showed several million dollars flowing from Conti‑linked wallets into wallets controlled by Black Basta. Researchers discovered a Russian national known by aliases like “GG,” “Tramp,” “Trump,” and “AA” was a key member of Conti and likely to be the founder of Black Basta.
Black Basta was a closed, high‑end ransomware-as-a-service (RaaS) cluster. A cluster is a network of specialists and partners coordinated around a brand, rather than a self-contained RaaS operation. This distinction matters because a cluster can ‘collapse’ as a brand with minimal disruption to the threats posed by its members. The underlying capabilities of a cluster are portable, and the same tooling and tactics can quickly reappear under new brands.
Public reporting places Black Basta’s debut in April 2022, shortly before Conti ceased operations. The group had roughly 100 victims in its first seven months and more than 500 victims worldwide by the time it attacked Ascension in May 2024.
Black Basta was known for attacking major enterprises and critical infrastructure, but Ascension was a watershed event for the group because it quickly increased the risk environment for the group. The attack disrupted operations at around 140 hospitals across 19 U.S. states and Washington, D.C., forcing a rapid return to paper workflows and ambulance diversions while staff struggled to get basic orders approved.
Black Basta posted its last victim on its leak site in January 2025. In February, an unknown actor going by the name “ExploitWhispers” leaked a huge cache of internal chat logs covering late 2023–2024. By March 2025 Black Basta was considered inactive, though its tactics and tools were seen in use by other brands.
ExploitWhispers announces the leak of Black Basta internal chats, via Bleeping Computer
Black Basta’s meltdown
The leaked chats show tensions emerge in the second half of 2024:
- Some Black Basta attacks had technical failures with encryption, making decryption impossible even if the ransom is paid.
- The QakBot disruption in August 2023 disrupted a major Black Basta delivery channel. The group struggled to find or build a replacement for nearly a year.
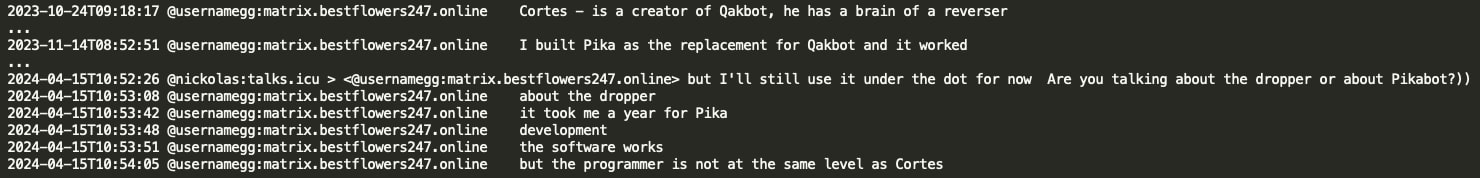
It took Black Basta a year to develop Pikabot after Qakbot’s takedown, via Trellix
- Black Basta leader GG was arrested in Armenia in June 2024. After three days in custody, he escaped to Russia while waiting for a court decision. He is safe from extradition, but this type of exposure can damage the brand of the group.
- Conversations around financial priorities and unfair pay and disagreements over which targets could be attacked revealed tension and resentment among affiliates.
- Attacks on Ascension were immediately followed by heightened public warnings about Black Basta. Members started talking about a rebrand.
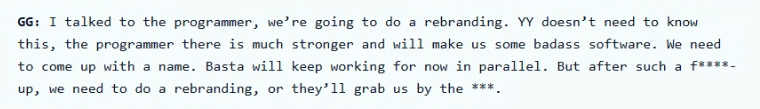
GG makes plans to drop rebrand Black Basta, via esentire
What happened next?
Not everyone working with Black Basta would have been affected by the collapse. Initial access brokers (IABs), bulletproof hosting providers and other *-as-a-Service providers or ‘gig’ workers would have kept operating with little interruption. Researchers speculate that Black Basta members and affiliates joined CACTUS and SafePay ransomware groups.
SafePay was first observed in September 2024, though it didn’t claim any victims until November of that year. The group’s activity and victim count grew in 2025, and its tools and tactics are like those used by Black Basta and Conti. SafePay is not a RaaS platform and would likely have only absorbed the strongest threat actors from Black Basta.
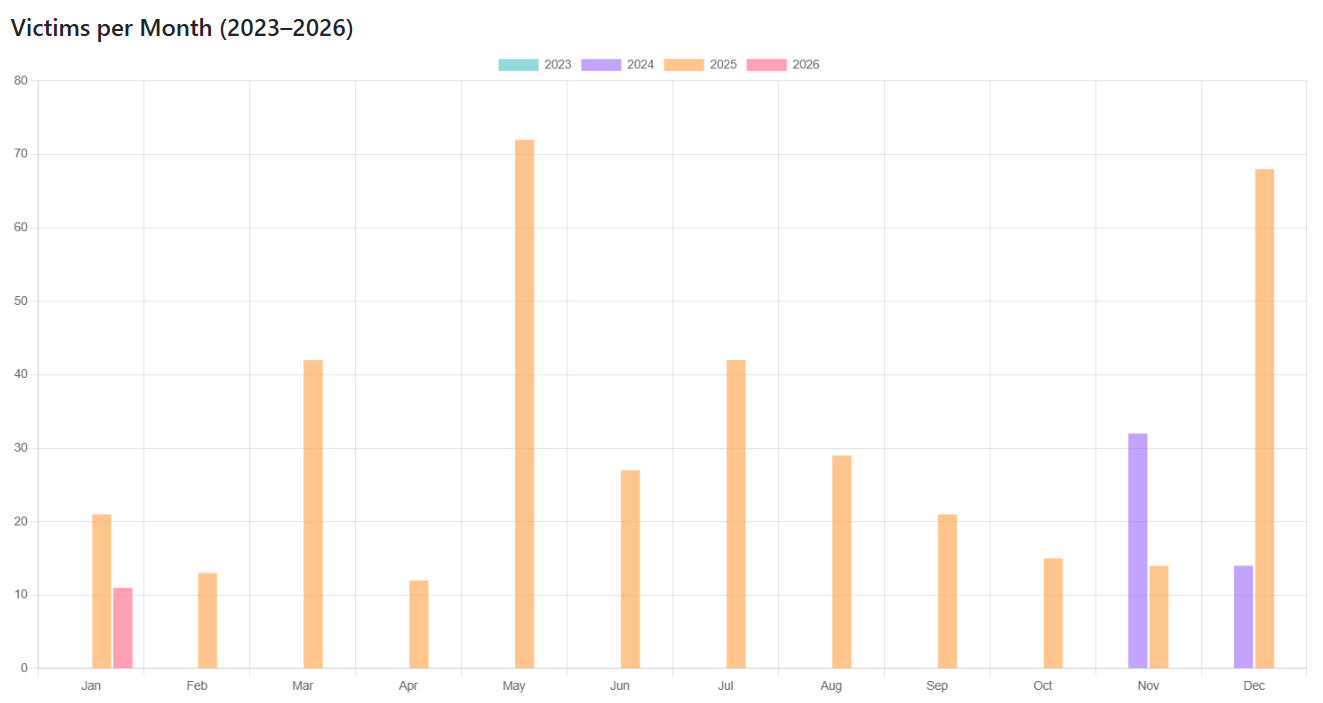
SafePay victim count by month and year, via Ransomware.live
SafePay is still active as of January 26, 2026.
CACTUS was discovered in the wild in March 2023 and operated concurrently with Black Basta. This group also had similar tactics and tools to those used by Black Basta and Conti, as well as a few other groups. CACTUS was last seen on March 21, 2025 and is now considered inactive.
There appears to be no direct evidence tying Black Basta members to either group, but there is evidence linking GG to at least one member of Cactus.
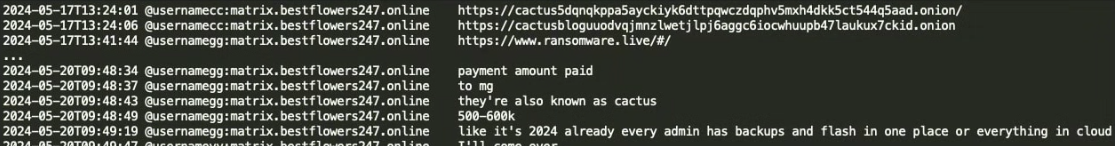
GG confirming he paid 'MG,' aka CACTUS, via Trellix
Ongoing investigation
While Black Basta was making its exit, investigators were finding multiple layers of forensic evidence linking identities to brands, locations and attacks. Early reports show key types of data being mined from these messages:
- Organizational structure and division of roles into leadership, operators, affiliates, specialists, etc.
- Details of day-to-day operations and workflows
- Tools, techniques and new social-engineering attacks like the Microsoft Teams campaigns
- Cryptocurrency wallet addresses and other data that revealed payment patterns and operational finance behavior
- Internal infrastructure discussions that analysts were able to connect to observed activity
- Messages that identified vulnerabilities and exploits that were priorities for the group
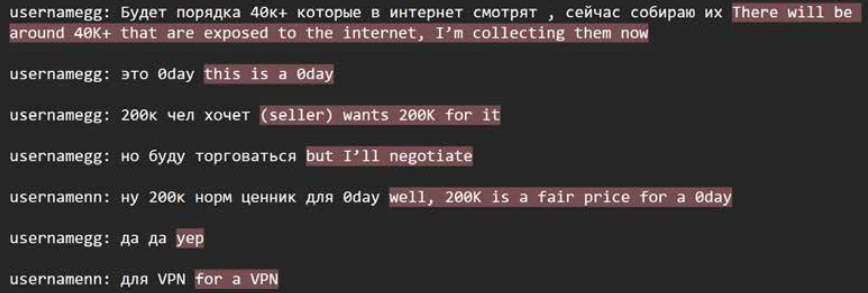
GG discusses buying a zero-day exploit, via LevelBlue
The leaked chats provided details on wallets, tools, timestamps, etc., but it was the correlation with disclosures and victim reporting that turned the data into real evidence. Wallet correlation helps trace payments and cash-out infrastructure, while timeline and tactic correlation helps match chat activity to specific intrusions. In the case of the Ascension attack, the chats showed GG involved in pre-attack access discussions and post-attack ‘firefighting.’ By combining what is known about the Ascension attack with what is found in the messages during the attack, investigators can show that GG knew about the planned attack on Ascension.
This is why it is so important that victims report attacks to the authorities. Every incident report is evidence.
What’s new?
In August 2025, Ukrainian police searched a residence, seized evidence, and questioned a suspect described as a “crypter”—someone whose job was to help ensure the malware used would evade antivirus detection. The legal status of this suspect is unclear.
The most recent law enforcement action took place on multiple fronts in January 2026. Investigators in Ukraine searched the homes of two suspects accused of doing “hash-cracker” work for Black Basta. Police also seized digital storage devices and cryptocurrency assets, which will hopefully contribute to ongoing investigations. The names of the suspects have not been released.

Police search suspect’s house and seize digital assets, via Cyber Police of Ukraine

Police take suspect into custody, via Ukraine Prosecutor General’s Office
Meanwhile, Germany’s federal police force publicly identified Oleg Evgenievich Nefedov as GG and announced he is wanted in connection with Black Basta activity. Nefedov was known to us before, but he has now been added to the Europol EU Most Wanted and an INTERPOL Red Notice has been issued.
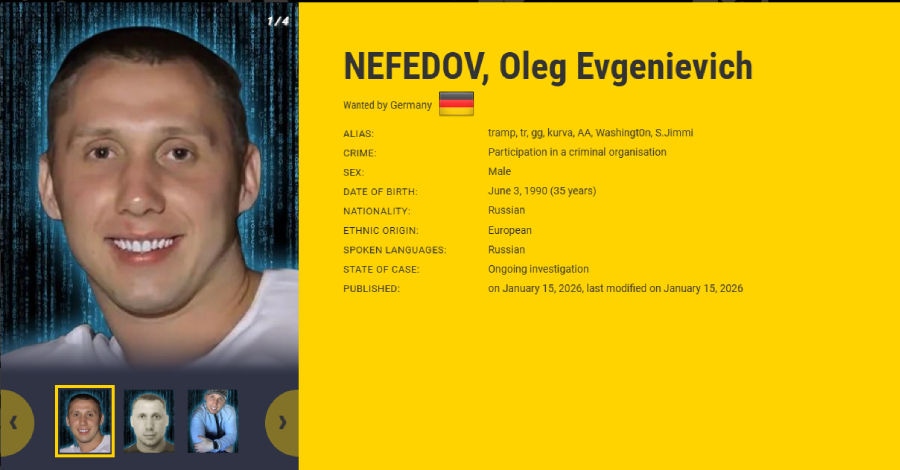
Oleg Evgenievich Nefedov listed in the Europol EU Most Wanted
What’s next?
We know there will be extensive forensic investigation into the assets seized in the January raids. When added to other evidence, we may find information on several other groups, or at least more members of the Black Basta cluster.
This is a classic example of how a threat survives even after the brand name is changed. Companies must maintain disciplined security practices. For example:
- Use phishing-resistant multifactor authentication (MFA) wherever possible.
- Lock down remote access (RDP/VPN) and admin tools.
- Patch internet-facing systems as soon as possible.
- Monitor for identity abuse and unusual helpdesk activity.
- Maintain offline/immutable backups with restore testing.
It is also important that companies and individuals report cyberattack incidents quickly. Every known detail is evidence that can help law enforcement pursue these criminals.
Did you know ...
Only Barracuda provides multi-faceted protection that covers all the major threat vectors, protects your data, and automates incident response. The BarracudaONE AI-powered platform protects your email, data, applications, and networks, and is strengthened by a 24/7 managed XDR service. It unifies your security defenses and provides deep, intelligent threat detection and response. Visit our website to see how it can help you protect your business.

Rapporto sulle violazioni della sicurezza e-mail 2025
Risultati chiave sull'esperienza e l'impatto delle violazioni della sicurezza e-mail sulle organizzazioni a livello mondiale
Iscriviti al blog di Barracuda.
Iscriviti per ricevere i Threat Spotlight, commenti del settore e altro ancora.

The MSP Customer Insight Report 2025
Uno sguardo globale su ciò di cui le organizzazioni hanno bisogno e vogliono dai loro provider di servizi gestiti per la sicurezza informatica





