
OWASP Top 10 Follows You Inside the Cloud
A security researcher identified some security vulnerabilities with Pocket – a service I love and use regularly. These were never exploited in the wild, (or so we hope). But they dispel a very common misconception: that web-based applications and web servers in the cloud are safe because the cloud infrastructure is safe.
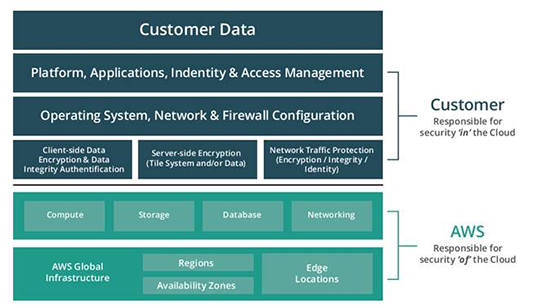
To be precise, the security of any applications, platforms, servers and even OS the tenant puts in the cloud is her own responsibility. The cloud infrastructure only provides security for the primitives – compute, storage, databases, etc.
Amazon puts this succinctly in the following infographic:
What the hack involved?
For the full details of the hack, see Multiple Vulnerabilities in Pocket. It’s a brilliant hack from one man and his only tool – the browser. Nothing else was needed. The hack also illustrates how multiple OWASP Top 10 Vulnerabilities were violated which could have resulted in:
- Grab file:///etc/passwd through 301 redirect to obtain autoprovisioned EC2 user’s home directory
- Grab ssh private keys from autoprovisioned EC2 user’s home directory using 301 redirect to file URI (after all, we’re running as root, we can read them).
- Use /server-status to obtain internal IP addresses.
- Spin up an EC2 instance in US-EAST-1 for 2 cents an hour.
- ssh into the private IP addresses for Pocket’s backend server using ssh private key.
- ???
- Profit!
Coming back to the OWASP Top10 prism, here is a list of several sections that were being violated:
A5 – Security misconfiguration
This was the genesis of the hack - apache mod_status and ExtendedStatus were enabled. These reveal a lot of details about Apache configuration, URLs and internal IP addresses. The researcher tricked Pocket into divulging this information by queuing a link to the localhost IP’s server status file that promptly gave away the details via the Pocket app. As I said, read the full article to get the complete picture on this.
A6 – Sensitive data exposure
Exploiting the Apache misconfiguration, the researcher could glean internal details about the environment like AWS instances details, credentials, etc. and details about the application itself as well.
A2-Broken Authentication and Session Management
“A very convenient feature of EC2 instances is Amazon’s instance metadata service. This service is accessible internally, without authentication, on any EC2 instance.”
A10-Unvalidated Redirects and Forwards
Researcher was able to leverage Pocket’s redirect mechanism to effect malicious redirects.
A4-Insecure Direct Object References
Researcher was able to reference internal implementation objects such as files and directories, via buggy protocol handlers combined with malicious redirects (e.g. Redirecting to file:///etc/passwd)
A1-Injection
Researcher was able to inject requests via HTTP to obtain OS level resources like /etc/passwd, /proc filesystem, etc ..
How do you protect your business critical web applications?
The Barracuda Web Application Firewall addresses the OWASP Top 10 amongst other things. Not only is it available in on-prem models, it is also available directly through the AWS and Azure Marketplaces. It can:
- Cloak revealing messages that can be used to identify the server, e,g, Apache, IIS, etc.
- Prevent sensitive data leakage via web applications
- Prevent malicious redirects as well OS command injections via web applications
For additional details, click here to see our OWASP Top 10 white paper (pdf).

The Ransomware Insights Report 2025
Risultati chiave sull'esperienza e l'impatto del ransomware sulle organizzazioni a livello mondiale
Iscriviti al blog di Barracuda.
Iscriviti per ricevere i Threat Spotlight, commenti del settore e altro ancora.

Sicurezza della vulnerabilità gestita: correzione più rapida, meno rischi, conformità più semplice
Scopri quanto può essere facile individuare le vulnerabilità che i criminali informatici vogliono sfruttare




