
LockBit to FBI: 'You can't stop me'
A strange and somewhat sad LockBit-related situation has developed over the last few days. @LockBitSupp, the presumed leader of the prolific LockBit ransomware group, published a formal response to Operation Cronos and the FBI. In a nearly 3,000-word document, LockBitSupp published his account of what happened, what was seized, what remains, and what he learned. We have the background on Operation Cronos and LockBit here.
I have paraphrased the notable points in the document and included some direct quotes from the author. This section includes comments from the LockBit response letter, not from Barracuda or other third-party sources.
What happened?
- LockBit servers were likely compromised due to vulnerabilities in PHP 8.1.2. Servers running this older version of PHP were the only servers affected.
- The compromise was likely due to CVE-2023-3824 but could have been something else. The servers now run PHP 8.3.3, and LockBit will reward the first person who finds and reports a CVE on this version. LockBit also offers a bug bounty program to support the security of the operation.
- The FBI acted against LockBit due to the compromise of Fulton County, Georgia. The stolen documents from Fulton County contain information about “Donald Trump’s court cases that could affect the upcoming U.S. election.” Negotiations with Fulton County had stalled. The documents were to have been released on the day of the seizure, which explains the timing of “the FBI attack.”
“… for 5 years of swimming in money I became very lazy … Due to my personal negligence and irresponsibility I relaxed and did not update PHP in time.”
What was seized?
- The FBI claims to have seized many LockBit assets, including 1000 decryptors. This amounts to about 2.5% of LockBit decryptors, most of which were protected and cannot be used by the FBI.
- The FBI seized the generated nicknames of various LockBit partners. These nicknames are not associated with real LockBit partners and will not lead to their identification. The FBI might believe they have arrested LockBit partners based on these nicknames, but this is incorrect.
- The source code of the web panel seized by the FBI was the only thing of value. The panel will now have to be decentralized across many servers to prevent future compromise.
“Leak of the panel source code was also happening at competitors, it didn't stop them from continuing their work, it won't stop me either.”
What remains?
- Dozens of operational LockBit domains are listed in the document, and most were in place before the seizure.
- LockBit will continue to give out data stolen from the attacked companies. After additional protection is added, there will be “no chance” of the seized decryption keys working.
- Fulton County data will be published if the ransom is unpaid by March 2, 2024.
“New affiliates can work in my affiliate program if they have a reputation on the forums, can prove that they are pentesters with post-payment, or by making a deposit of 2 bitcoins”
Lessons learned and advice to others:
- Do not just update PHP. Change hosts, change passwords, and migrate everything. There is no guarantee that the FBI does not have a 0-day or another way to re-hack compromised servers.
- High quality cryptocurrency laundering protects ransomware operators.
“What conclusions can be drawn from this situation? Very simple, that I need to attack the .gov sector more often and more, it is after such attacks that the FBI will be forced to show me weaknesses and vulnerabilities and make me stronger. By attacking the .gov sector you can know exactly if the FBI has the ability to attack us or not.”
LockBitSupp also spends some time trolling law enforcement …
“The FBI designer should work for me, you have good taste, I especially liked the new preloader … I wonder why the alpha, revil, hive blogs were not designed so nicely?”
“… beautiful advertising from the FBI, which is that my affiliates and I earn together hundreds of millions of dollars, and that no FBI with their assistants can scare me and stop me, the stability of the service is guaranteed by years of continuous work.”
… and complaining about them.
“… it would be interesting to see the video of the arrest, where at their homes, Lamborghinis and laptops with evidence of their involvement in our activities, but I somehow think we will not see it … FBI arrested random people to get a certificate of merit from the management”
“I never donated to anyone, it would be nice if the FBI showed the transaction so I could check on the blockchain where they drew such conclusions from and why they claim it was me who did it”
“You can accuse me of anything without proving anything, and there is no way I can refute it, because there are no transactions and bitcoin wallets.”
There’s a lot in this statement, but much of it is redundant, and all of it is written by a criminal trying to protect his ransomware operation from losing money. I doubt the public can know what’s true, but we should assume that no ransomware threat is ever fully shut down. People who are not arrested will continue to operate, and unseized resources will be sold or shared with other threat actors. If we built a family tree for ransomware, we would find the same names in multiple places. If we go back far enough, we might find a floppy disk circa 1989. When the Operation Cronos task force announced the LockBit seizures, it was reasonable to assume that LockBit wasn’t gone. The FBI referred to its operation as a ‘disruption,’ and @LockBitSupp told us we were too late to stop him. Since we can’t know exactly what’s true or false, let's just unpack some of the claims in LockBitSupp’s rebuttal:
Claim: LockBit has stolen data on Donald Trump’s Georgia indictment
LockBit has already released roughly two dozen files allegedly stolen from Fulton County. Leaking documents ahead of the ransom negotiation is common because it shows the victim and other threat actors that the threat is real. Brian Krebs of KrebsOnSecurity points us to the reporting of George Chidi of The Atlanta Objective.
According to Chidi, the leaked files are said to include:
- A sealed record related to a child abuse case.
- A sealed motion in the murder trial of Juwuan Gaston demanding the state turn over confidential informant identities.
- The identities of jurors serving on the trial of the rapper Jeffery “Young Thug” Williams.
“The screenshots suggest that hackers will be able to give any attorney defending a criminal case in the county a starting place to argue that evidence has been tainted or witnesses intimidated, and that the release of confidential information has compromised cases,” Chidi wrote. “Judge Ural Glanville has, I am told by staff, been working feverishly behind the scenes over the last two weeks to manage the unfolding disaster.”
LockBitSupp has not yet proven he has data about the Trump indictment, but the Gaston, Williams, and Trump cases are all in the Superior Court of Fulton County.
Claim: FBI seizure intended to stop the leak of Trump-related data
The U.S. Federal Bureau of Investigation has been targeting LockBit for years, and the Europol statement referenced a “months-long infiltration” of the group. The LockBit attack on Fulton County was discovered on January 27, 2024, and continued for weeks before Operation Cronos was announced on February 20. Fulton County already had two prior deadlines for the breach. Here’s a brief timeline:
- Late January: LockBit claims responsibility for the Fulton County attack, which took down many county systems.
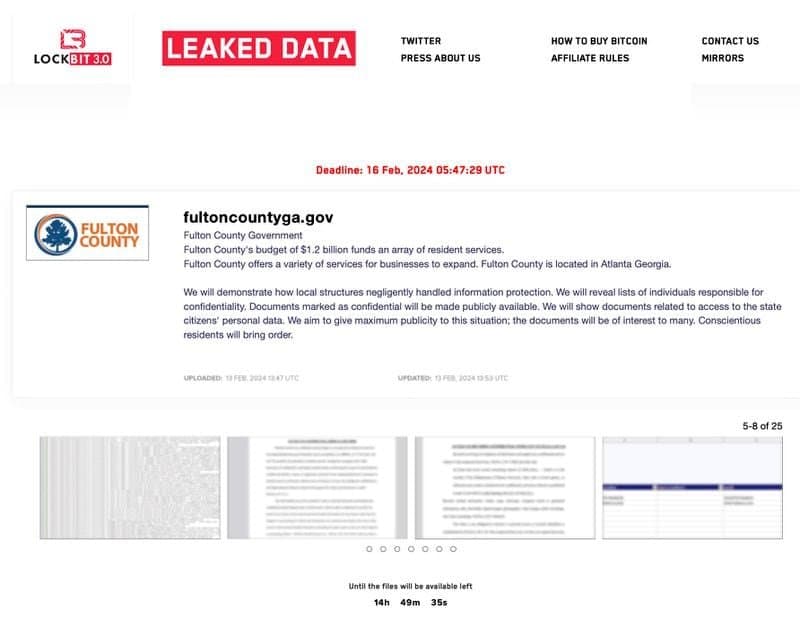
- Early February: Fulton County officials acknowledge the intrusion.
- Mid-February: LockBit posts screenshots of seemingly legitimate county documents and information about servers maintained by the county. The county is given a deadline of February 16, 2024 at 5:47:29 UTC to pay the ransom and prevent the publication of the stolen data. This post was later removed from LockBit’s site without explanation. County officials later said say they did not pay the hackers.
- February 20: LockBit’s websites are seized, Operation Cronos is revealed, and two people are arrested and charged for LockBit affiliation. LockBitSupp posts on X (formerly Twitter) that “the world has realized the danger too late.”
- February 24: LockBitSupp announces the group is operational again and has new countdown timers for Fulton County and other victims. LockBit now says the deadline for Fulton County is March 2.
It’s probably true that law enforcement would want to prevent confidential documents from being released, especially regarding any legal issues of a former U.S. President. It seems less probable that this would be the reason for the timing of Operation Cronos. In September 2023, researchers announced that LockBit was responsible for one in six attacks on U.S. government offices. Would law enforcement and federal authorities have waited if LockBit could have been disrupted sooner?
Brian Krebs questions this claim as well:
“… if the NCA and FBI really believed that LockBit never deleted victim data, they had to assume LockBit would still have at least one copy of all their stolen data hidden somewhere safe.”
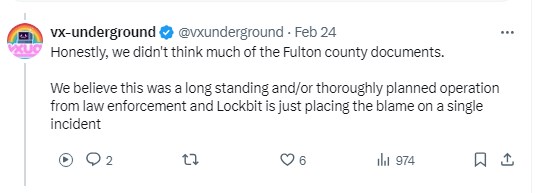
And even @vxunderground dismisses the claim:
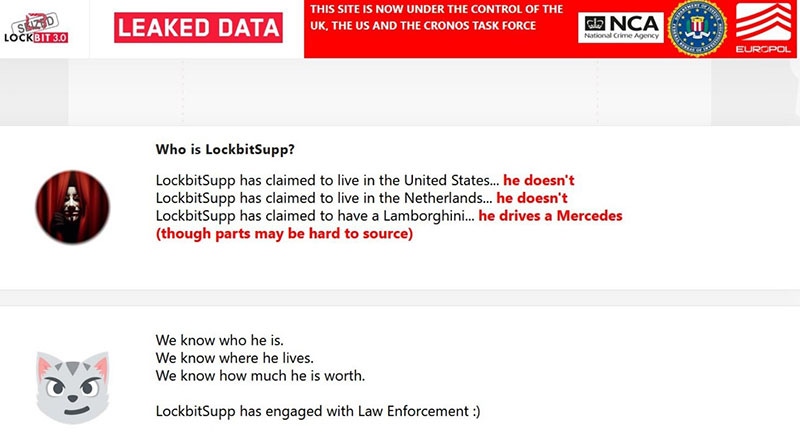
Claim: Law enforcement does not know the identity of LockBitSupp
This was published on LockBit servers after Operation Cronos was announced:
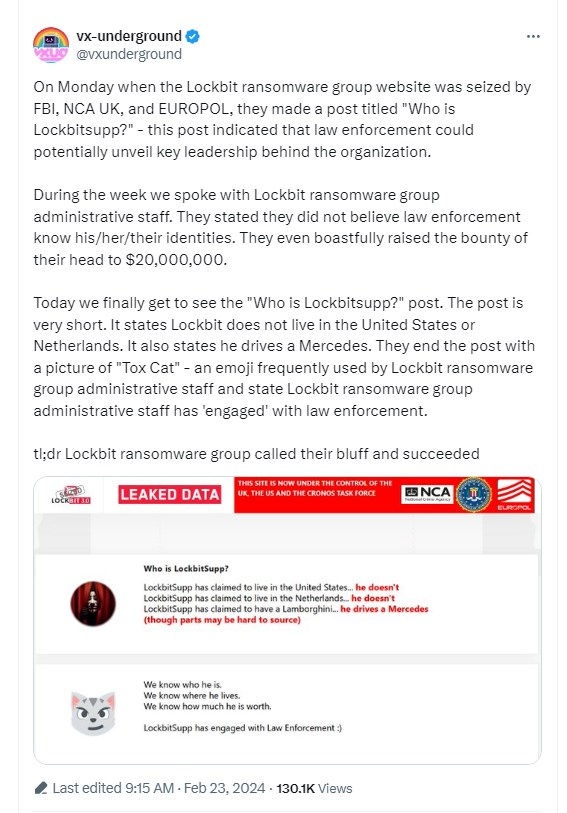
On February 23, @vxunderground posted that LockBit operatives denied working with the FBI and didn’t believe that law enforcement knew their identities:
LockBitSupp also repeatedly states that the FBI has arrested “random people”, and that law enforcement would have published his identity if they could. KrebsOnSecurity also contacted LockBitSupp using the ToX Messenger information in the rebuttal letter:
Asked why he was so certain the FBI doesn’t know his real-life identity, LockBitSupp was more precise.
“I’m not sure the FBI doesn’t know who I am,” he said. “I just believe they will never find me.”
The purpose of ‘we know who he is’ probably has nothing to do with his identity and everything to do with reducing his ability to recruit affiliates and partners. Without the affiliates and scaled-up infrastructure, LockBit is not the threat it once was.
What do we do now?
Stay vigilant. Be on alert for things like fake offers of LockBit decryption keys. These offers could be phishing attacks using websites, social media, or emails with malicious attachments. Other attacks like malicious web advertisements and drive-by downloads can be used in the same way. Follow the law enforcement guidelines for accessing a LockBit decryption key.
If you receive a link to free decryption keys, FBI rewards, or anything else weird and related to LockBit, report it to your system administrator. If you’re using Barracuda Email Protection, you may be able to use the Barracuda Outlook Add-In for this.
All people and companies remain at risk of LockBit and other attacks. Barracuda recommends a three-step approach to protecting yourself from ransomware:
- Protect your credentials.
- Secure your applications.
- Back up your data.
We also offer a complete cybersecurity platform that protects your company against advanced threats and automated attacks.
To learn more about specific threat actors and data breaches, follow our blog here.

The Ransomware Insights Report 2025
Risultati chiave sull'esperienza e l'impatto del ransomware sulle organizzazioni a livello mondiale
Iscriviti al blog di Barracuda.
Iscriviti per ricevere i Threat Spotlight, commenti del settore e altro ancora.

Sicurezza della vulnerabilità gestita: correzione più rapida, meno rischi, conformità più semplice
Scopri quanto può essere facile individuare le vulnerabilità che i criminali informatici vogliono sfruttare





