RansomHub. Because every abandoned affiliate needs a home.
Sometimes life just isn’t fair. One day, you’re an intrepid little ALPHV/BlackCat affiliate going about your business and trying to make a dishonest living. The next, your partner-in-cybercrime scores big and closes shop, leaving you with no brand, no infrastructure, and no dignity. Where do you go from there?
No worries, all abandoned affiliates are welcome to join RansomHub, a relatively new ransomware brand that many experienced threat actors now call home.
RansomHub announced itself on February 2, 2024, with this post on the RAMP criminal forum:
“We welcome you to join our affiliate raas program RANSOMHUB.
We considered all the pros and cons of previous affiliate programs and created the next generation of ransomware.
We have noticed that some affiliates have been seized by the police or have escaped from fraudulent activity causing you to lose your funds. We have adopted a new strategy, You can send your wallet to the chat room and send the decryptor after you confirm the payment. You don’t have to worry about your funds security.
Our fixed rate is 10%, and you pay us when you receive the money.”
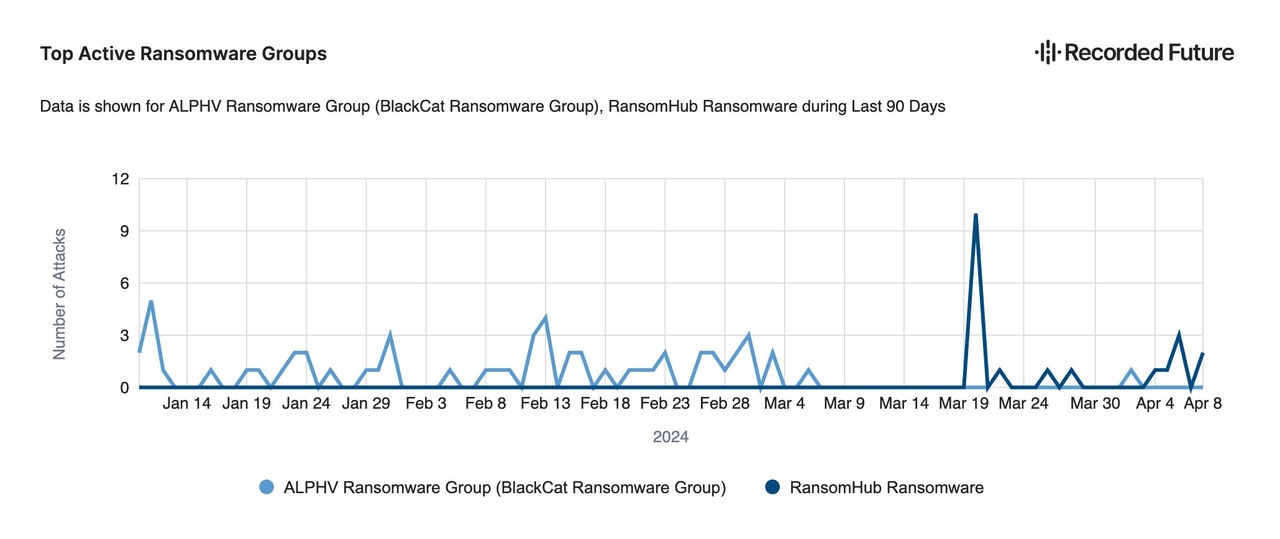
Eight days later, RansomHub claimed their first victim, and in April, they claimed their largest.
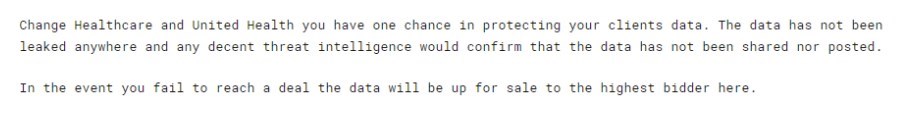
Change Healthcare was notified that it would have to pay a second ransom to protect its data since ALPHV had stolen the first.
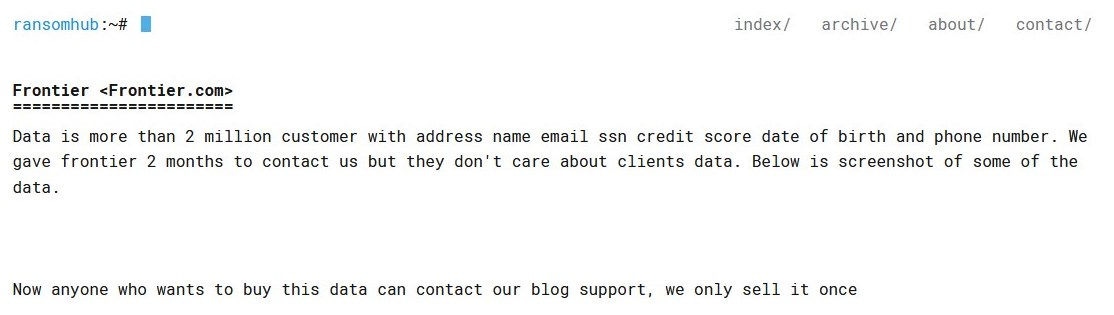
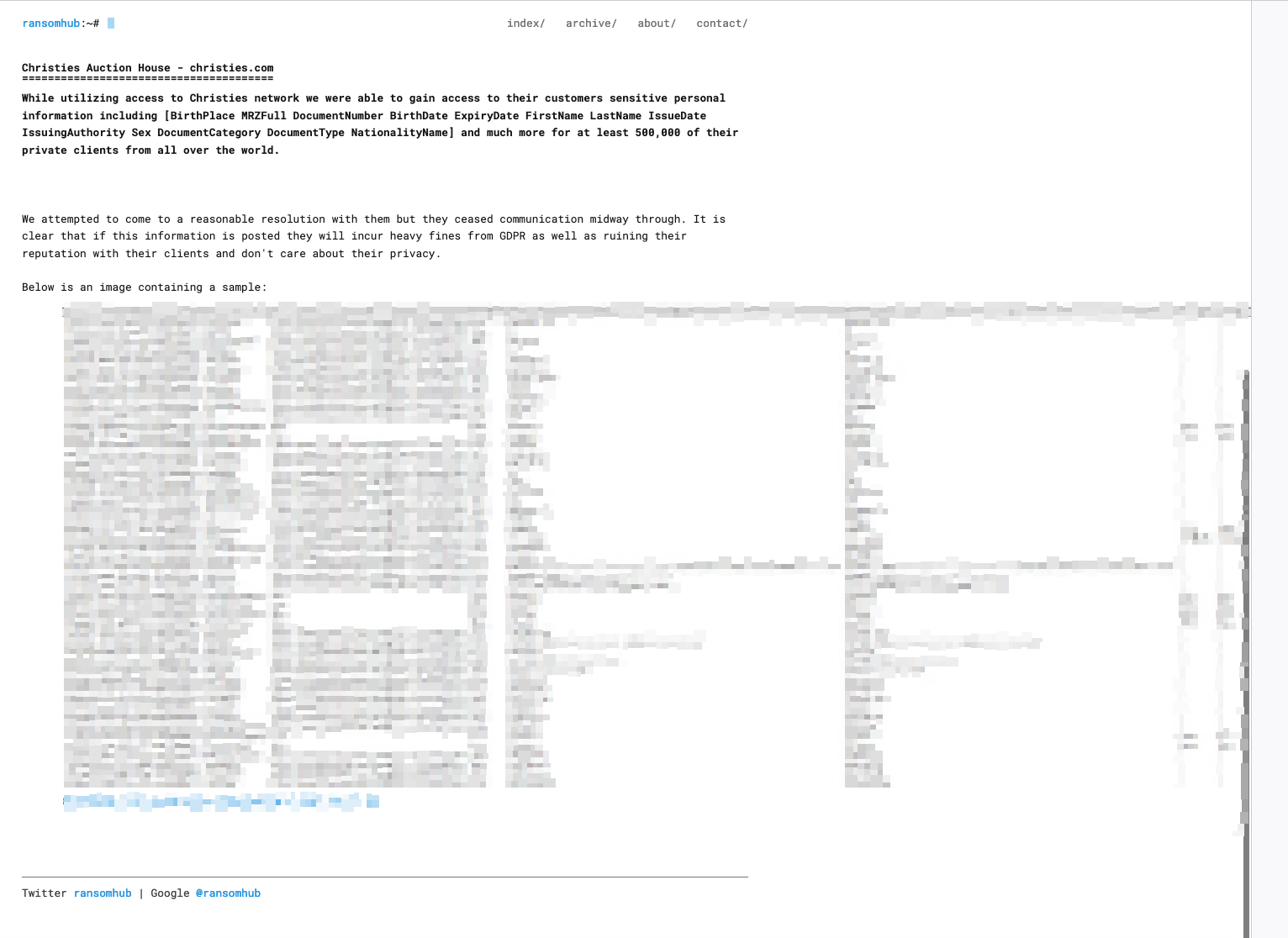
To date, RansomHub has claimed 74 (known) victims, including Frontier Communications and Christie's Auction House.
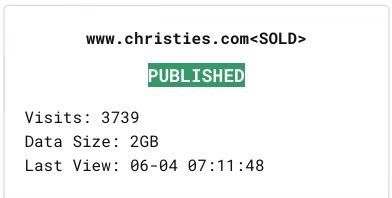
RansomHub allegedly sold the Christie’s Auction House data on June 4.
The Christie’s breach may have some unexpected impact on consumer protection laws due to a class action lawsuit that includes some intriguing types of alleged harm:
“…data brokering comprises a $200bn market … Christie’s clients can no longer voluntarily sell their personal data in it at full value because that data has already been exposed by the RansomHub breach.”
The lawsuit also alleges harm by partial sets of data being combined to create “fullz” packages, which are complete profiles of an individual. A threat actor with a fullz package can do serious damage to the profiled victim.
This will probably not be litigated, but it would be interesting to see how an expanded scope of harm would affect disclosure laws, liability, etc. This article has more information on the lawsuit.
Who is RansomHub?
There isn’t much known about the affiliates and operators of RansomHub. The brand operates as a RaaS, and it took advantage of the void left by ALPHV to recruit some experienced affiliates. Additionally, RansomHub operators have structured their payment scheme to prioritize paying the affiliate first. RansomHub’s rapid growth can be attributed, in part, to this payment arrangement.
RansomHub affiliates operate globally, but they explicitly state that they do not target countries within the Commonwealth of Independent States (CIS), Cuba, North Korea, and China. This is a common practice among Russian-affiliated ransomware groups. The group also announced itself on the Russian Anonymous Market Place, also known as the RAMP crime forum.
Like most ransomware groups, RansomHub appears to be driven by financial gain and not any political ideology or socio-economic purpose. They go after victims in target-rich countries and industries where they think they’ll get the highest ransoms. Most victims are in the United States, United Kingdom, Germany, Canada, and Australia. The group likes to attack healthcare, finance, and manufacturing sectors.
By April 2024, RansomHub was the fifth most active ransomware group, and they were claiming nearly as many victims each month as LockBit and Play
RansomHub family tree
There was early speculation that RansomHub was a rebrand of ALPHV. While both threat groups were active from February to April, RansomHub attacks increased shortly after ALPHV shut down. Dmitri Smilyanets was one of the first to illustrate this timeline:
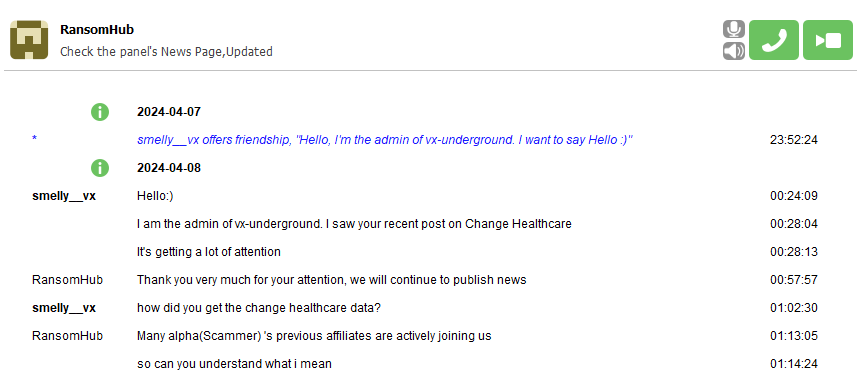
Then there was the obvious connection of Change Healthcare. ALPHV was paid, but RansomHub had the data. This was addressed in a forum conversation between vx underground and the RansomHub operator:
So at this point it looks like Notchy went to RansomHub with the Change Healthcare data, and he was joined by many other ALPHV affiliates.
Then there are the tactics, techniques, and procedures (TTPs) used by both ALPHV and RansomHub. Researchers have observed significant similarities in the operational methods and tools used by RansomHub and ALPHV threat actors. This includes the deployment methods, ransom note styles, and encryption algorithms. Both groups use a similar command and control (C2) infrastructure, including overlapping IP addresses and domains. And RansomHub ransomware includes code that appears to be directly copied from ALPHV ransomware.
You may recall that the ALPHV family tree goes back to GandCrab, which shut down in 2019. The GandCrab operators are thought to have moved on to REvil ransomware, which appeared in April 2019. Both groups were active from April to June of that year, had similar ransomware code, and used some of the same infrastructure.
REvil went offline in late 2021, and many of its affiliates and TTPs appeared to show up in DarkSide attacks shortly thereafter. DarkSide shut down in May 2021, shortly after the Colonial Pipeline incident, which was declared a national security issue. It re-emerged as Blackmatter in July 2021 but shut down again in November 2021, citing new regulations that made it difficult to collect ransoms.
And as we mentioned in an earlier post, Blackmatter is thought to have rebranded to ALPHV/BlackCat. This brings us back to RansomHub’s recruitment of ALPHV affiliates.
Researchers have found code similarities between RansomHub and ALPHV, Cyclops, and Knight (Cyclops 2.0).
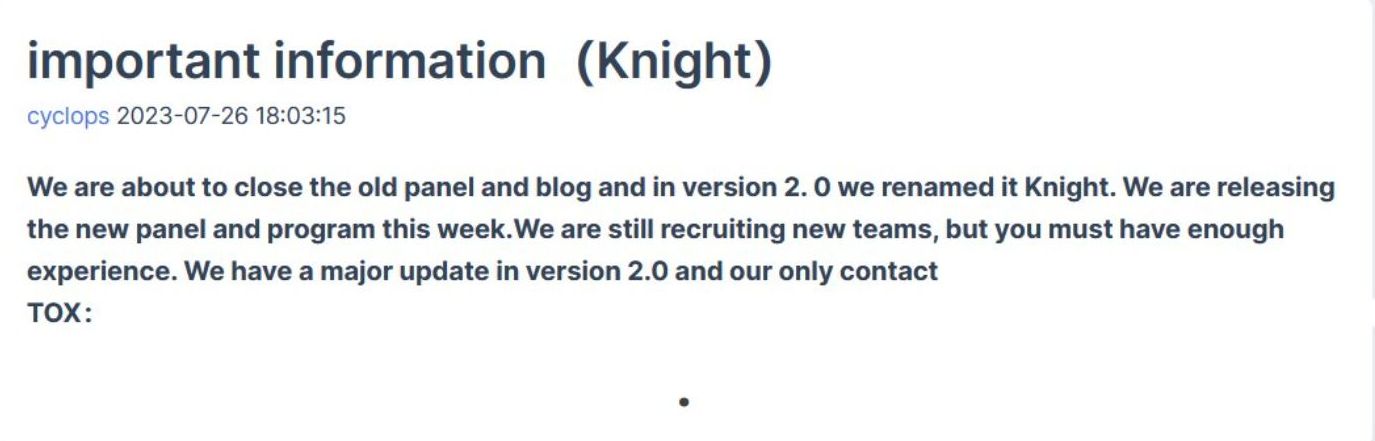
Cyclops ransomware emerged as a RaaS in 2023 and became known for developing custom strains tailored to exploit vulnerabilities in the target network. The group used advanced encryption methods and double extortion, and could attack Windows, Linux, and macOS. The Cyclops brand didn’t last long though because it publicly announced it would rebrand to Knight ransomware when the next version was launched.
There were then allegations that Knight had connections with Babuk and LockBit, which Knight has denied in this interview with SuspectFile:
“We don’t claim to have anything to do with them, it’s some media nonsense they’re reporting to get attention, and we have a completely different code than they do and use a different development language.”
The Knight ransomware group put their software up for sale in February 2024, around the same time RansomHub was born.
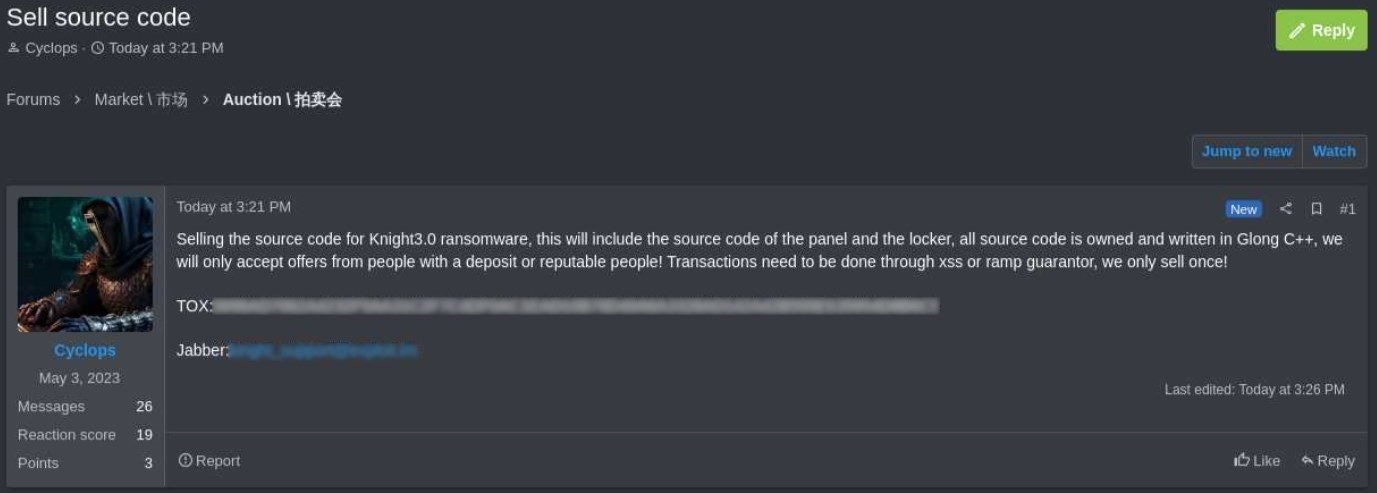
Many researchers now believe RansomHub used the Knight source code to create its own strain. RansomHub software may be considered a rebrand of Knight software, but the group isn’t a rebrand of the other.
Researchers learn most of this information by examining timelines, TTPs, and other types of intelligence. Code samples, IP addresses, and similarities in ransom notes and other details provide clues to the origins and identities of these threats. Threat operators change brand names, and threat actors change affiliations, but their attacks almost always start with stolen credentials, poorly secured remote access points, or vulnerabilities and exploits.
Protect your business
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) Stop Ransomware website can help you prevent ransomware attacks. You should review this site for information on emergency communications, bad practices, and proper ransomware attack response. Also, make sure you’re following the standard best practices, such as regular data backups and timely patch management.
Barracuda offers complete ransomware protection and the industry’s most comprehensive cybersecurity platform. Visit our website to see how we defend email, network, applications, and data.

The Ransomware Insights Report 2025
Risultati chiave sull'esperienza e l'impatto del ransomware sulle organizzazioni a livello mondiale
Iscriviti al blog di Barracuda.
Iscriviti per ricevere i Threat Spotlight, commenti del settore e altro ancora.

Sicurezza della vulnerabilità gestita: correzione più rapida, meno rischi, conformità più semplice
Scopri quanto può essere facile individuare le vulnerabilità che i criminali informatici vogliono sfruttare