Biometrics and beyond: Exploring the current state of MFA
Multifactor authentication (MFA) can be a complicated subject, with recent controversies such as Twitter/X charging for SMS-based MFA hitting the headlines. And despite the efficacy of MFA in protecting against cyberattacks, adoption remains far from universal.
Prove Identity’s State of MFA 2023 report found that less than half (48%) of employers mandate that employees use MFA at work. Only 19% of consumers surveyed said they have to use MFA across their work accounts. Despite the bad press, MFA remains a vital tool for securing your IT estate and your users’ credentials.
Brushing up on MFA basics
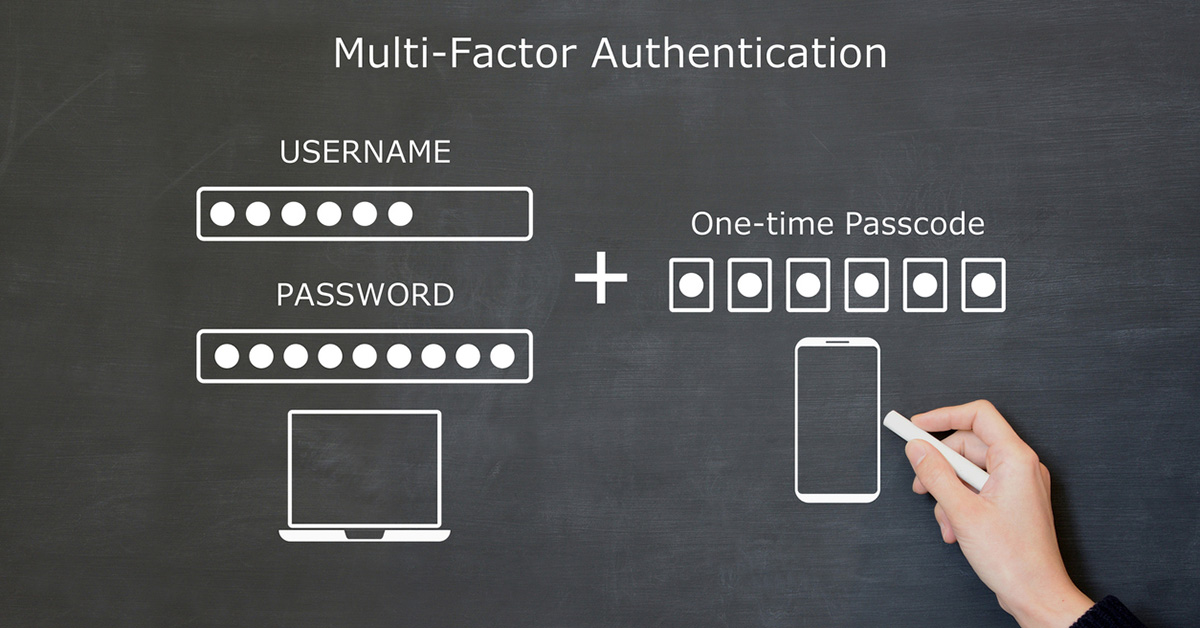
We brought you up to speed with the basics of MFA back in 2020, but things change quickly in the cyber realm, and it’s always good to have a refresher. MFA is a method of protecting your credentials by adding another factor to enter or provide before you can log in to an account. There are three types of factors to choose from:
- Something you know: This includes passwords, a PIN, and also security questions, such as the classic ‘mother’s maiden name’ request.
- Something you have: This can be a token or a smartcard. Increasingly this can be a registered mobile device or email account that can receive a one-time code or password.
- Something you are: This refers to biometric factors such as fingerprints, facial recognition, or iris scans.
When an account requires you to use MFA to log in, it will ask for the ‘something you know’ factor and then demand that you verify it with at least one of the other factors. This extra layer of protection is highly effective for blocking successful breaches. Even if an attacker has gained access to your credentials, it’s very difficult for them to falsify a token or biometric factor.
How effective is MFA?
Multifactor authentication is still one of the best ways to protect your — or your employees — credentials. Alex Weinert, VP Director of Identity Security at Microsoft, believes that “based on our studies, your account is more than 99.9% less likely to be compromised if you use MFA.”
That’s a pretty encouraging statistic. However, MFA’s effectiveness at stopping attacks has led to campaigns that try to take advantage of MFA fatigue — when users accept spoof MFA requests without close examination — with Microsoft reporting more than 382,000 such attacks in 2022. This has prompted the company to update its Microsoft Authenticator app to reduce the risk. There have also been adversary-in-the-middle phishing attacks that try to compromise MFA access. Good cyber security hygiene is still important, even when using MFA. While these attacks are significant, there are solutions: using certificate-based authentication and conditional access can minimise the risk of a successful attack of this kind.
MFA is also increasingly seen as a basic part of corporate security, not least by regulators and advisory bodies. In the United Kingdom, the Information Commissioner’s Office, among others, advises some form of MFA to reinforce passwords as a bare minimum for effective security.
However, adoption of MFA is a bit of a battlefield — as with all security measures, it only works if you make it workable and as frictionless as possible for your users. The UK’s National Cyber Security Centre has some good advice on moving beyond passwords without driving users crazy. The reality is that most people are already using at least two-factor authentication for basic online services. The State of MFA 2023 report found more than 60% of consumers saying they use MFA to access online banking, healthcare portals and apps, and insurance accounts. It’s something most people have experience with outside of work, even if only to decline the option to turn on MFA.
Make sure that you streamline MFA experiences for the best chance of increasing rates of adoption. Using biometric identification via mobile phone instead of one-time passwords is a top enabler for encouraging MFA adoption. If you can make it easy for your people, you will find a lot less resistance to using MFA, and ultimately increase your protection against all breaches that involve stolen credentials.

The Ransomware Insights Report 2025
Risultati chiave sull'esperienza e l'impatto del ransomware sulle organizzazioni a livello mondiale
Iscriviti al blog di Barracuda.
Iscriviti per ricevere i Threat Spotlight, commenti del settore e altro ancora.

Sicurezza della vulnerabilità gestita: correzione più rapida, meno rischi, conformità più semplice
Scopri quanto può essere facile individuare le vulnerabilità che i criminali informatici vogliono sfruttare