
Threat Spotlight: Email Malware Impersonates Secure Bank Messages
 Everyone seems to be on a heightened alert following the recent Equifax data breach and probably keeping a closer eye on bank statements and credit reports for good measure. You might even be more likely to open an email from your bank these days that perhaps you would’ve ignored in previous months. Monitoring bank accounts and credit reports is always a good idea; however, we’ve seen a recent run of alarming email threat patterns that should make you think twice before you act on an email from your bank.
Everyone seems to be on a heightened alert following the recent Equifax data breach and probably keeping a closer eye on bank statements and credit reports for good measure. You might even be more likely to open an email from your bank these days that perhaps you would’ve ignored in previous months. Monitoring bank accounts and credit reports is always a good idea; however, we’ve seen a recent run of alarming email threat patterns that should make you think twice before you act on an email from your bank.
In this month’s Threat Spotlight, we dissect an email attack that is impersonating a “secure message” from financial institutions, which we’re quickly finding to be a growing trend. Here’s what we’ve found:
Highlighted Threat:
Secure Bank Message Impersonation — email attack delivered by spoofed messages from financial institutions
The Details:
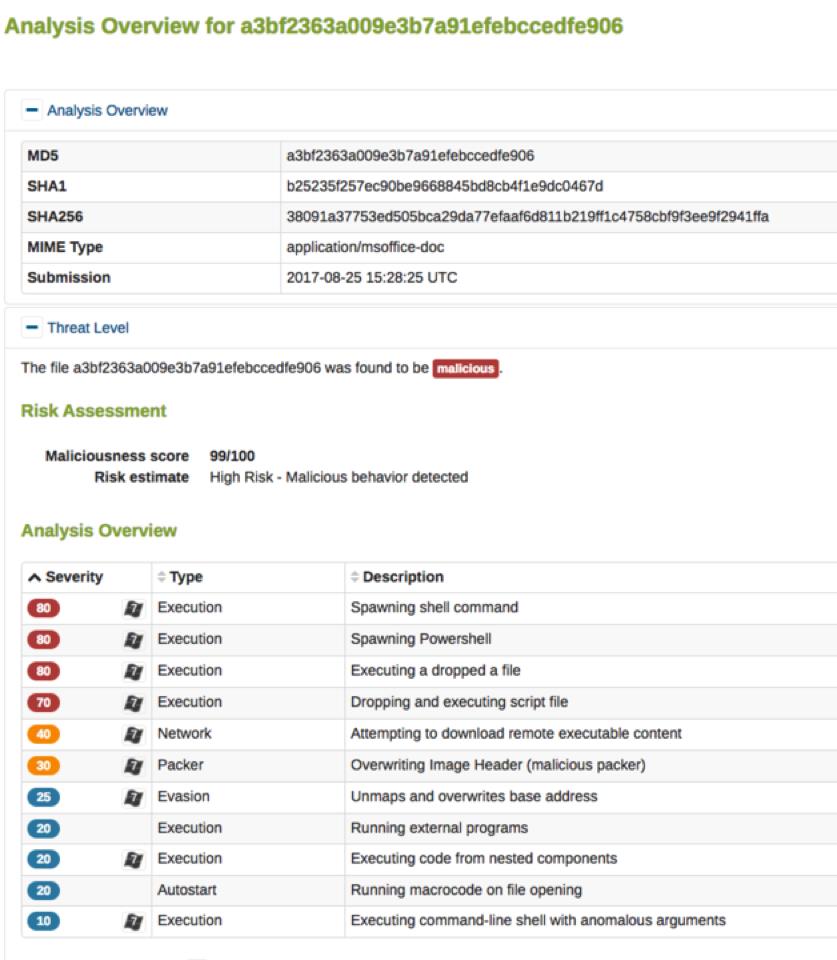
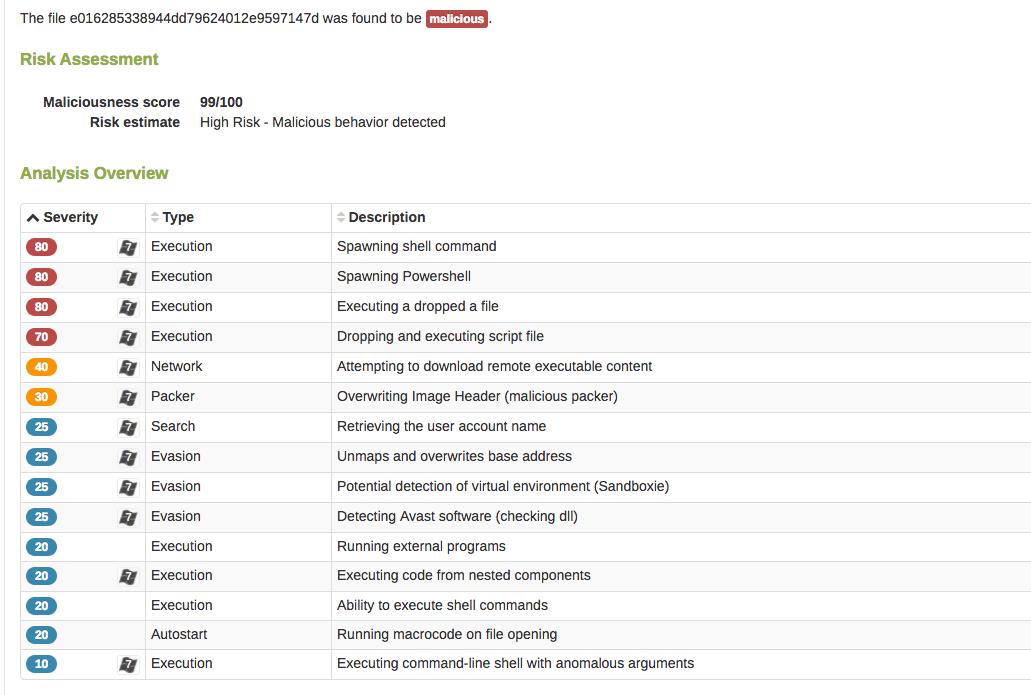
Impersonation is one of the most common tactics used in email attacks for one simple reason — it works. This particular instance is no different, and we’ve been tracking a consistent stream of emails from attackers that are impersonating secure messages from financial institutions. While these threats appear to be real messages from actual banks, it’s important to understand that the financial institutions mentioned in the emails below haven’t been hacked; however, their names are being used by criminals to persuade recipients to act on the messages.
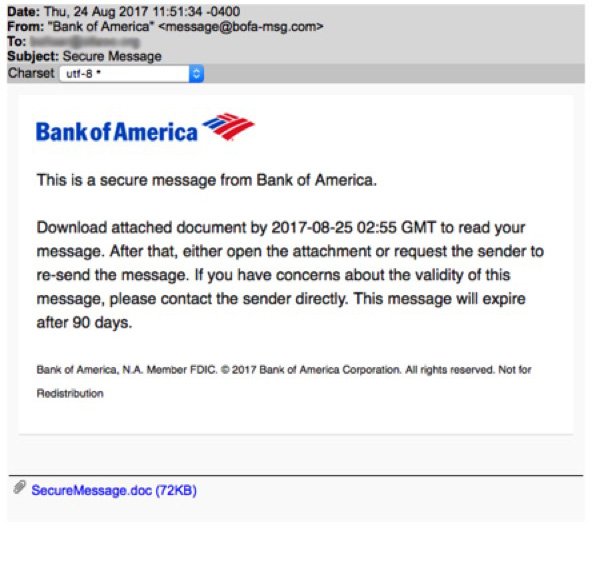
In this first example, the message appears to be a request from Bank of America that instructs the recipient to either download an attached document or reply back to the sender.
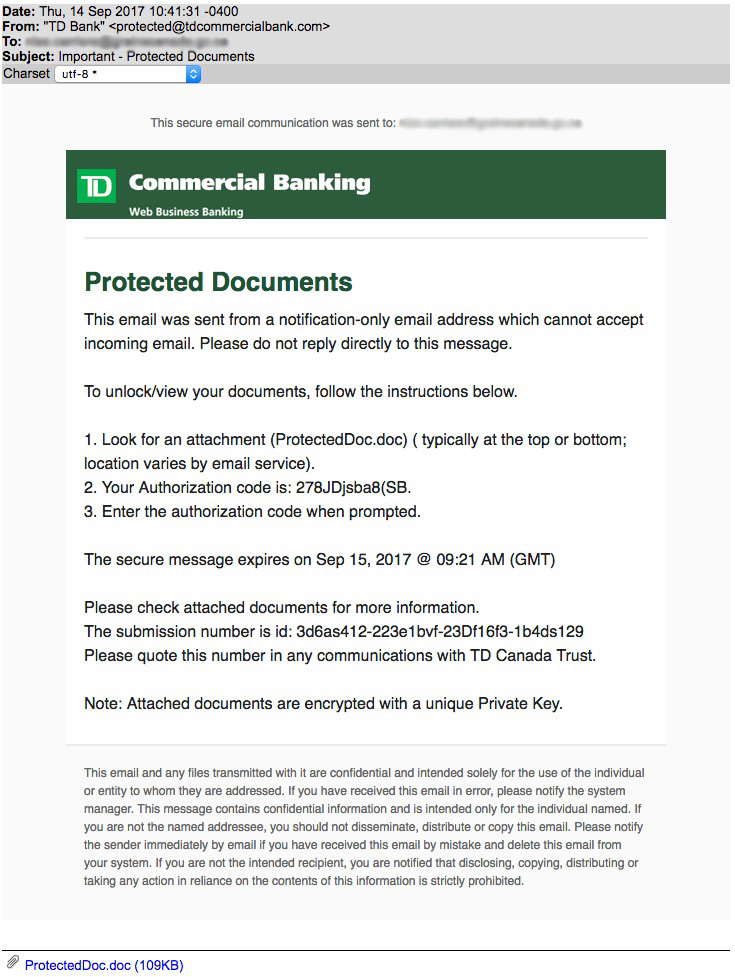
In this last example, you can see that the first step states, “You must be connected to the internet to view the secure email.”
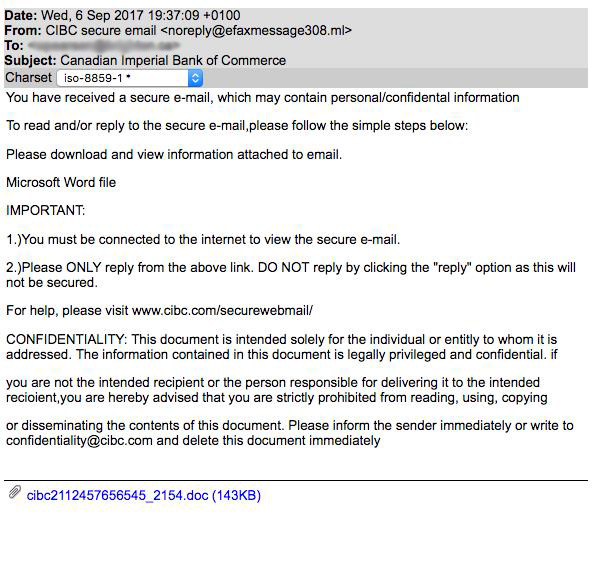
 Ultimately, criminals are registering domains that appear like a legitimate bank domain, and they go unnoticed because recipients either don’t know what to look out for or because most email clients only show the sender’s name and not the full domain. Criminals use this tactic to entice recipients into opening and acting on emails, but it can be easily spotted by trained users. Sadly, these threats are exploiting the trust between banks and their customers.
Ultimately, criminals are registering domains that appear like a legitimate bank domain, and they go unnoticed because recipients either don’t know what to look out for or because most email clients only show the sender’s name and not the full domain. Criminals use this tactic to entice recipients into opening and acting on emails, but it can be easily spotted by trained users. Sadly, these threats are exploiting the trust between banks and their customers. To recap, the techniques used in this attack are:
• Impersonation: Attackers impersonate real financial institutions, exploiting inherent trust between these institutions and their customers.
• Email spoofing: The email domains used in this attack are spoofed to appear like real emails that customers might receive from an actual bank.
• Phishing: Attackers send emails as a “secure bank” message that asks users to act on the requests made by the criminals.
Take Action:
User Training and Awareness — Employees should be regularly trained and tested to increase their security awareness of various targeted attacks. Simulated attack training is by far the most effective form of training. Always check the domains on emails asking for things from you, including clicking and inputting information.
Layering employee training with an email security solution that offers sandboxing and advanced threat protection should block malware before it ever reaches the corporate mail server. Additionally, you can deploy anti-phishing protection with Link Protection to look for links to websites that contain malicious code. Links to these compromised websites are blocked, even if those links are buried within the contents of a document.
Real-Time Spear Phishing and Cyber Fraud Defense — Barracuda Sentinel is a cloud service that utilizes AI to learn an organization’s communications history and prevent future spear phishing attacks. It combines three powerful layers: an artificial intelligence engine that stops spear phishing attacks in real time and identifies the most high-risk individuals inside the company; domain fraud visibility using DMARC authentication to guard against domain spoofing and brand hijacking; and fraud simulation training for high-risk individuals.
 Fleming Shi is the Senior Vice President of Technology at Barracuda, where he leads the company’s cloud-enabled microservices technology innovation and integrations across the entire security and data protection portfolio. Connect with him on LinkedIn here.
Fleming Shi is the Senior Vice President of Technology at Barracuda, where he leads the company’s cloud-enabled microservices technology innovation and integrations across the entire security and data protection portfolio. Connect with him on LinkedIn here.

The Ransomware Insights Report 2025
Risultati chiave sull'esperienza e l'impatto del ransomware sulle organizzazioni a livello mondiale
Iscriviti al blog di Barracuda.
Iscriviti per ricevere i Threat Spotlight, commenti del settore e altro ancora.

Sicurezza della vulnerabilità gestita: correzione più rapida, meno rischi, conformità più semplice
Scopri quanto può essere facile individuare le vulnerabilità che i criminali informatici vogliono sfruttare





